Mobile Device Management
Strong Control + Weak Control
|
Device Registration · Device activation invitation |
|
Device Info. Retrieval · Device information |
|
Device Policy · Device configuration policy |
|
Device Running · Device track |
|
Remote Control
· Lock/erase/logout device |
|
Recycle Device · Unbind device/restore factory
settings |
Mobile Application
Lifecycle Management
 Enterprise App Store
Enterprise App Store
 App Whitelist/Blacklist
App Whitelist/Blacklist
 Unified Release Mobile App
Unified Release Mobile App
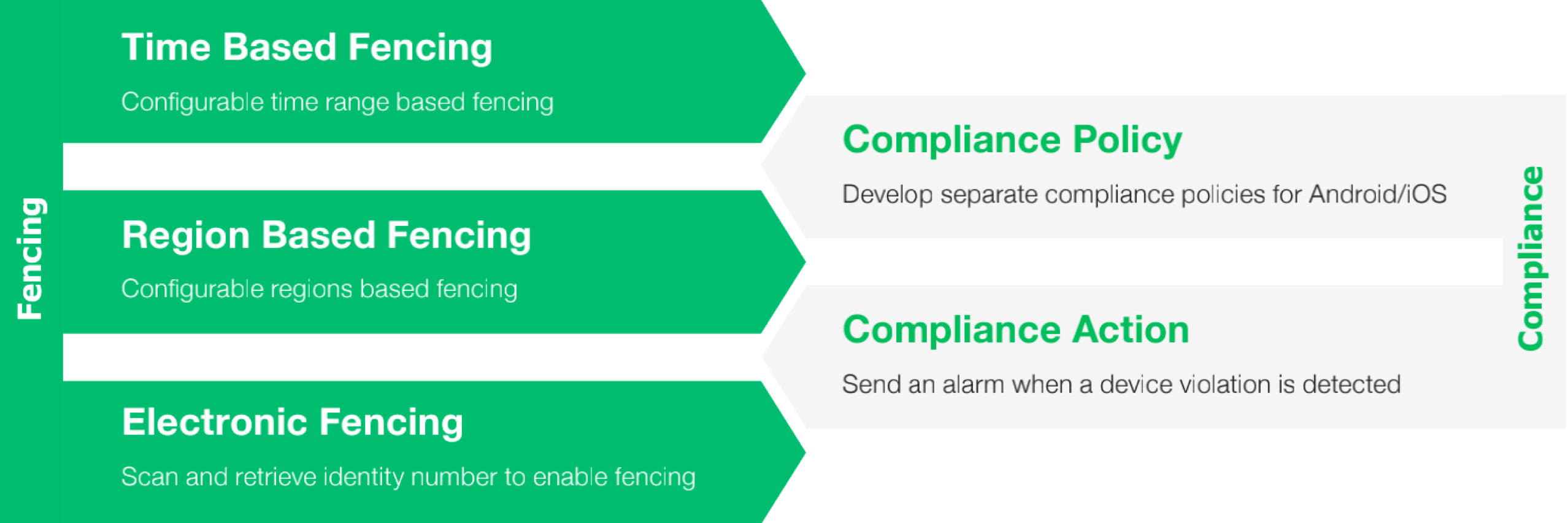
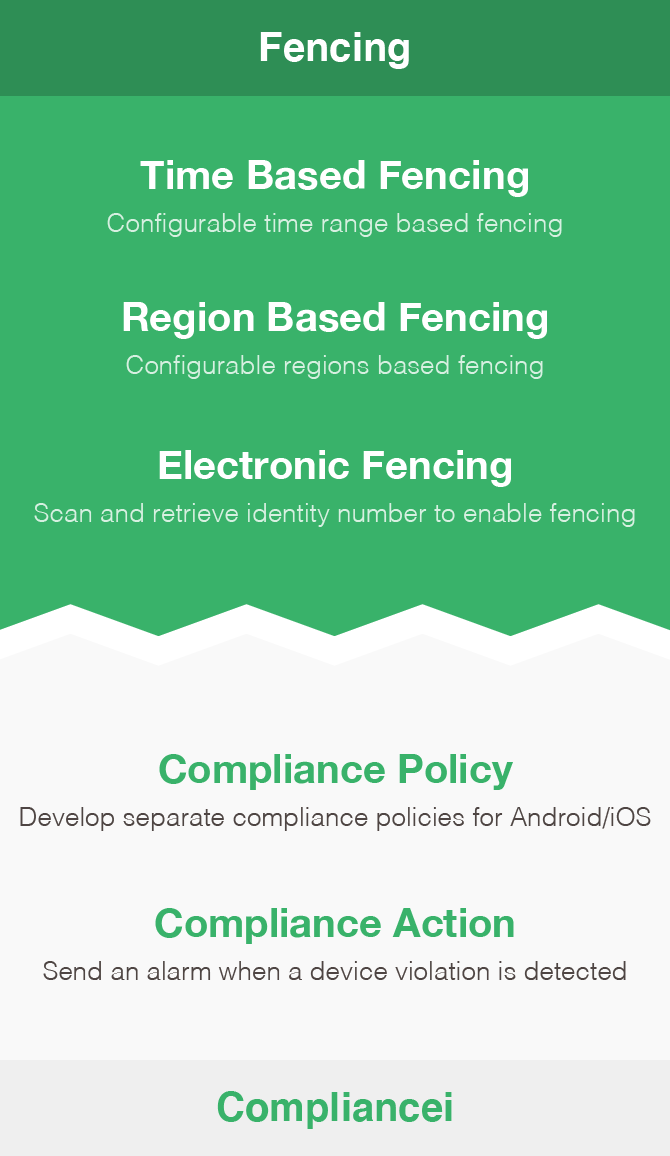
 App Fencing Configuration
App Fencing Configuration
 Enterprise App DLP
Enterprise App DLP
 Secure App Gateway
Secure App Gateway
Build Enterprise Mobile
Security Framework

|
Network Security · Encrypted tunnel |

|
User Security · User center |

|
Environment Security · Risk detection |

|
Device Security · Device registration |

|
Content Security
· Content push |

|
Application Security · Authorized release |
Unified Endpoint Management
Unified Endpoint Management can manage mobile devices, PCs&Macs, wearables and IoT devices.
Mobile Devices
PCs & Macs

Wearables

IoT Devices













